Latest Articles
Need boots that conquer mud, rain, and long hours on your feet without sacrificing comfort? The UA Micro G® Valsetz Reaper Waterproof by Under Armour, showcased in this video, delivers unmatched performance and versatility. Built for adventurers, outdoor workers, and fans of tactical style, let’s dive into why these boots are a must-have for tackling life’s toughest challenges.
Why the UA Micro G® Valsetz Reaper Waterproof?
Under Armour is synonymous with cutting-edge athletic innovation, and these boots are no exception. Blending advanced technology with a rugged, tactical design, they’re engineered to thrive in harsh environments while keeping you comfortable and agile.
Need boots that conquer mud, rain, and long hours on your feet without sacrificing comfort? The UA Micro G® Valsetz Reaper Waterproof by Und...
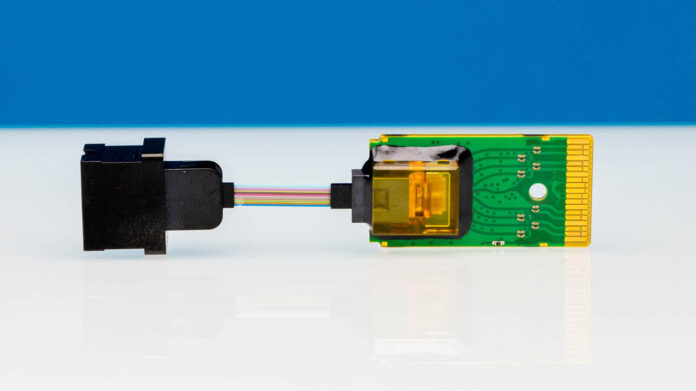
A few days ago we posted our Going 800Gbps at up to 1000km with the Marvell COLORZ 800 piece and in that we briefly showed inside two other modules. One we already featured in Inside a 100G QSFP28 DAC. The other, the 100G SR4 QSFP28 module is certainly more complex than the 100G QSFP28 DAC, so we wanted to show that as well. Usually it is not the best idea to take apart optical modules if you want to ensure they keep working, so we decided to sacrifice one for STH.
A few days ago we posted our Going 800Gbps at up to 1000km with the Marvell COLORZ 800 piece and in that we briefly showed inside two other ...
Intel has new network adapters, at least in some respects, with the Intel E830 200GbE and E610 10GbE NICs. These two new series are expected to roll-out over 2025 and be Intel’s new PCIe Gen4 NICs moving forward. This is a launch where it really paid to read into the details versus the headline features.
Intel has new network adapters, at least in some respects, with the Intel E830 200GbE and E610 10GbE NICs. These two new series are expected...
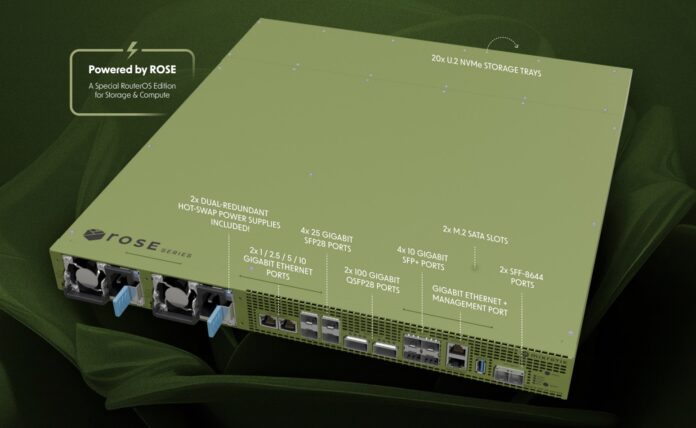
The MikroTik RDS2216 combines a U.2 NAS, a 100GbE, 25GbE, and 10GbE switch, and a lightweight Arm server into a single machine. As one might expect, there are some caveats, but this looks like one of the coolest devices we have seen this year. Just when you think you have the machine figured out, it appears as though you do not as it just has more features.
MikroTik RDS2216 Inbound with 20x U.2 NVMe and 100GbE on Arm
Things that we were not expecting when we woke up this morning:
- MikroTik making a hybrid NVMe NAS, router, switch, server
- The server to be green
Yet both seem to be true. Let us start with the front(?) of the box. Here you can see the green color along with five columns of four U.2 drives. Given this is a 1U box, those cannot be 15mm drives and, instead are likely 7mm U.2 drive bays.
The MikroTik RDS2216 combines a U.2 NAS, a 100GbE, 25GbE, and 10GbE switch, and a lightweight Arm server into a single machine. As one might...
Today we are continuing our microSDXC card series with the Samsung Pro Plus 1TB microSDXC card. Flash media cards are an area where the technology has been around for a long time, and folks have had both positive and negative experiences. Some folks swear by Samsung cards, so we wanted to include them, but we could not get a 1.5TB to 2TB card. We are also looking at the newer 180MB/s card as there is a Pro Plus that is a 160MB/s card. It is quite confusing.
Note: We purchased our 1TB card on Amazon (affiliate link)
The Samsung Pro Plus 1TB microSDXC Card
Since these cards are tiny, we get a lot more packaging than we get device.
Let us quickly get to what this card is. We have V30, A2, and U3 markings. If you need a quick cheat sheet see What All of the Markings on SD microSD and microSDXC Cards Mean. While this is not the highest performing card, it is designed to be higher performing and actually run applications from it, unlike the SanDisk 1.5TB Ultra we looked at previously.
Even though this drive is tiny in size, at 1TB it can store a lot of data. We regularly see PCs equipped with 256GB to 1TB capacity M.2 SSDs which is in this capacity range.
Here is a quick look at the contact side of the card:
Unlike the SanDisk models, we cannot see a package exposed on this side.
Bundled with this card, we get a microSDXC to SD adapter in Samsung’s bright white.
via servethehome
Today we are continuing our microSDXC card series with the Samsung Pro Plus 1TB microSDXC card. Flash media cards are an area where the tech...
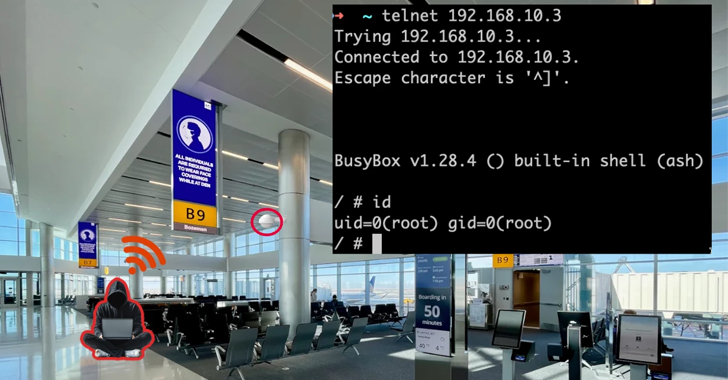
Cybersecurity firm Arctic Wolf has disclosed details of an ongoing cyber campaign targeting Fortinet FortiGate firewall devices with exposed management interfaces on the public internet.
Fortinet confirmed the exploitation of this zero-day vulnerability after cybersecurity researchers from Arctic Wolf observed mass exploitation campaigns targeting publicly exposed Fortinet firewalls since November 2024.
Cybersecurity firm Arctic Wolf has disclosed details of an ongoing cyber campaign targeting Fortinet FortiGate firewall devices with exposed...
A critical 7-Zip zero-day exploit has been allegedly leaked by a hacker who is an individual operating under the alias “NSA_Employee39” on X, which allows attackers to execute arbitrary code on a victim’s machine when opened or extracted with the latest version of 7-Zip.
This disclosure poses significant cybersecurity risks, particularly in the context of Infostealer malware proliferation and potential supply chain attack vectors.
A critical 7-Zip zero-day exploit has been allegedly leaked by a hacker who is an individual operating under the alias “NSA_Employee39” on X...
Cybersecurity researchers have discovered several security flaws in the cloud management platform developed by Ruijie Networks that could permit an attacker to take control of the network appliances.
"These vulnerabilities affect both the Reyee platform, as well as Reyee OS network devices," Claroty researchers Noam Moshe and Tomer Goldschmidt said in a recent analysis. "The vulnerabilities, if exploited, could allow a malicious attacker to execute code on any cloud-enabled device, giving them the ability to control tens of thousands of devices."
Cybersecurity researchers have discovered several security flaws in the cloud management platform developed by Ruijie Networks that could pe...
A Serbian journalist had his phone first unlocked by a Cellebrite tool and subsequently compromised by a previously undocumented spyware codenamed NoviSpy, according to a new report published by Amnesty International.
"NoviSpy allows for capturing sensitive personal data from a target's phone after infection and provides the ability to turn on the phone's microphone or camera remotely," the company said in an 87-page technical report.
An analysis of forensic evidence points to the spyware installation occurring when the phone belonging to independent journalist Slaviša Milanov was in the hands of the Serbian police during his detention in early 2024.
Some of the other targets included youth activist Nikola Ristić, environmental activist Ivan Milosavljević Buki, and an unnamed activist from Krokodil, a Belgrade-based organization promoting dialogue and reconciliation in the Western Balkans.
The development marks one of the first known instances where two disparate highly invasive technologies were used in combination to facilitate snooping and the exfiltration of sensitive data.
NoviSpy, in particular, is engineered to harvest various kinds of information from compromised phones, including screenshots of all actions on the phone, targets' locations, audio and microphone recordings, files, and photos. It's installed using the Android Debug Bridge (adb) command-line utility and manifests in the form of two applications -
- NoviSpyAdmin (com.serv.services), which requests extensive permissions to collect call logs, SMS messages, contact lists, and record audio through the microphone
- NoviSpyAccess (com.accesibilityservice), which abuses Android's accessibility services to stealthily collect screenshots from email accounts and messaging apps like Signal and WhatsApp, exfiltrate files, track location, and activate camera
Exactly who developed NoviSpy is currently not known, although Amnesty told 404 Media that it could have either been built in-house by Serbian authorities or acquired from a third-party. Development of the spyware is said to have been ongoing since at least 2018.
"Together, these tools provide the state with an enormous capability to gather data both covertly, as in the case of spyware, and overtly, through the unlawful and illegitimate use of Cellebrite mobile phone extraction technology," Amnesty International noted.
The non-governmental organization further noted that the Serbian Security Information Agency (BIA) has been publicly linked to the procurement of spyware tools since at least 2014, using various offerings such as FinFisher's FinSpy, Intellexa's Predator, and NSO Group's Pegasus to covertly spy on protest organizers, journalists and civil society leaders.
In a statement shared with the Associated Press, Serbia's police characterized the report as "absolutely incorrect" and that "the forensic tool is used in the same way by other police forces around the world."
Responding to the findings, Israeli company Cellebrite said it's investigating the claims of misuse of its tools and that it would take appropriate measures, including terminating its relationship with relevant agencies, if they are found to be in violation of its end-user agreement.
In tandem, the research also uncovered a zero-day privilege escalation exploit used by Cellebrite's universal forensic extraction device (UFED) – a software/system that allows law enforcement agencies to unlock and gain access to data stored on mobile phones – to gain elevated access to a Serbian activist's device.
The vulnerability, tracked as CVE-2024-43047 (CVSS score: 7.8), is a user-after-free bug in Qualcomm's Digital Signal Processor (DSP) Service (adsprpc) that could lead to "memory corruption while maintaining memory maps of HLOS memory." It was patched by the chipmaker in October 2024.
Google, which initiated a "broader code review process" following the receipt of kernel panic logs generated by the in-the-wild (ITW) exploit earlier this year, said it discovered a total of six vulnerabilities in the adsprpc driver, including CVE-2024-43047.
"Chipset drivers for Android are a promising target for attackers, and this ITW exploit represents a meaningful real-world example of the negative ramifications that the current third-party vendor driver security posture poses to end-users," Seth Jenkins of Google Project Zero said.
"A system's cybersecurity is only as strong as its weakest link, and chipset/GPU drivers represent one of the weakest links for privilege separation on Android in 2024."
The development comes as the European arm of the Center for Democracy and Technology (CDT), alongside other civil society organizations such as Access Now and Amnesty International, sent a letter to the Polish Presidency of the Council of the European Union, calling for prioritizing action against abuse of commercial surveillance tools.
It also follows a recent report from Lookout about how law enforcement authorities in Mainland China are using a lawful intercept tool codenamed EagleMsgSpy to gather a wide range of information from mobile devices after having gained physical access to them.
Earlier this month, the Citizen Lab further revealed that the Russian government detained a man for donating money to Ukraine and implanted spyware, a trojanized version of a call recorder app, on his Android phone before releasing him.
via thehackernews
A Serbian journalist had his phone first unlocked by a Cellebrite tool and subsequently compromised by a previously undocumented spyware cod...
Popular Posts
-
Since extended reality entered the enterprise, many leaders have been speculating about a future where wearables will replace the computer s...
-
Often abbreviated to RHEL, Red Hat Enterprise Linux has just reached version number 9.5 after 24 years on the market. While continuing to pr...
-
Proxmox has gained tremendous popularity in 2024. So many home lab enthusiasts, SMBs, and enterprise environments are looking at their opti...
-
Woah, cool Hummer! Isn’t it just! Although, we hate to be pedantic (we don’t really, pedantry is very satisfying), but this isn’t actually a...
-
A critical 7-Zip zero-day exploit has been allegedly leaked by a hacker who is an individual operating under the alias “NSA_Employee39” on X...